If you do any kind of penetration testing or bug bounty hunting from your home PC, then as a necessity you will be sending malicious-looking traffic to your target. If your target happens to be protected by Akamai or CloudFlare, and you don’t take any special precautions, then unfortunate things may happen. Unfortunate, as in your home IP gets blocked from half the sites on the internet.
To avoid this, you need to make your web traffic look like it came from a different IP address than it actually did. This means using some kind of proxy server. There are a few different ways you can do this, but my preferred way is to use a virtual private server (VPS) rented out from a cloud provider.
If you are proxying your traffic through a cloud VPS and you manage to get blocked by Akamai, then not only will your home IP address not be affected, but you can also spin up a new VPS with a new IP address and carry right on from where you left off. You can even use the excellent Axiom project to automate spinning up new VMs and then deleting them when you know longer need them.
SSH port forwarding
To forward traffic from our local PC to the VPS we will be using the dynamic port forwarding feature of SSH. This allows you to create a socket on your local machine which acts as a SOCKS proxy; all applications using the proxy have their traffic sent through the SSH connection to the SSH server, which then sends it on to its actual destination.
To set up dynamic port forwarding, you pass the -D flag to SSH, followed by the
port number you want to use for the proxy server. To use port 8081, you would use
a command like this:
ssh -D 8081 <user>@<host>
Or if you’re using Axiom:
axiom-ssh <name> -D 8081
Here, <name> is the name Axiom assigned to the VPS.
You can also use the -C flag to enable compression if you have a slow connection.
For fast connections this can actually decrease performance, however, so choose
appropriately.
Setting up ZAP
To get OWASP ZAP to use the proxy, open Tools -> Options, and click on “Connection” in the left-hand pane.
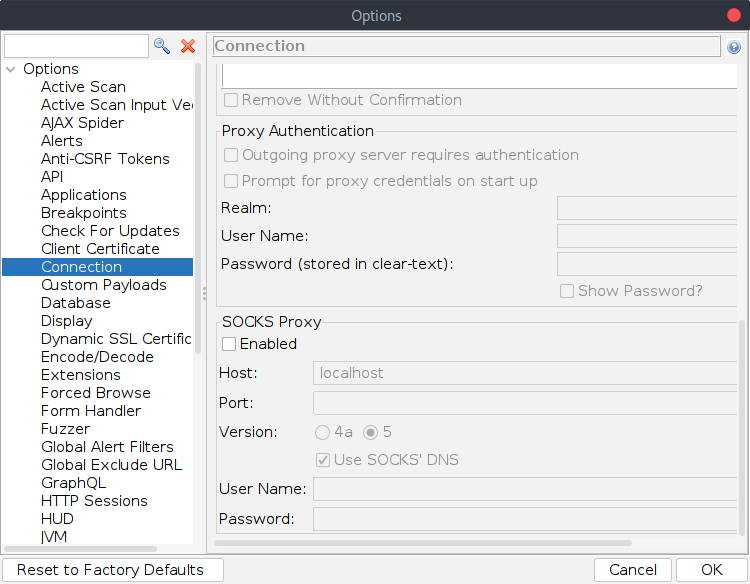
Check the “Enabled” check box in the “SOCKS Proxy” section, set the host to localhost, and set the port to the port number you used in the SSH command. On my installation, the options widgets were too wide for the window, meaning I couldn’t see the port number. If you have the same problem, you might need to scroll horizontally or resize the window so that you can see it.
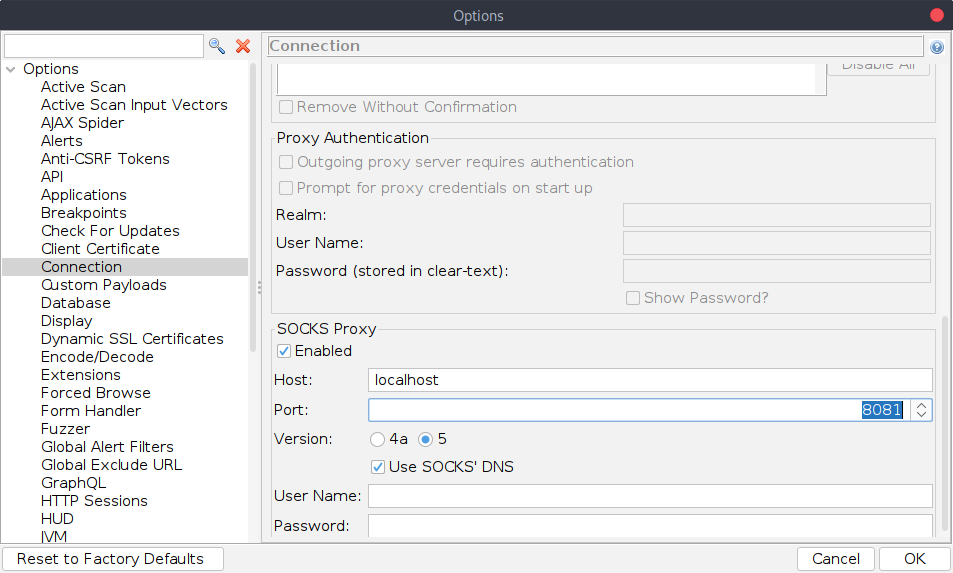
When you are done, click OK.
Testing the connection
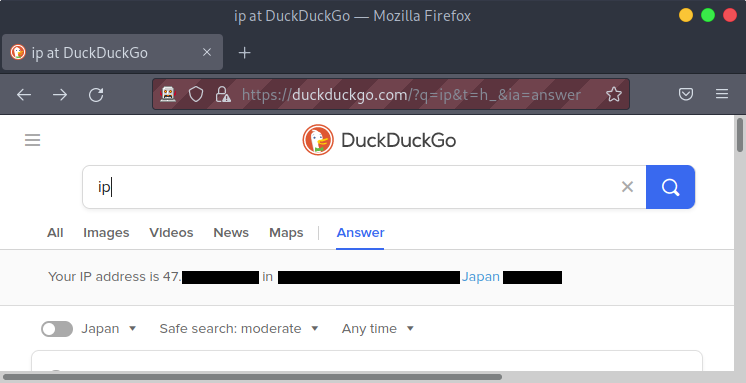
To test the connection, start a manual exploration session in ZAP, and then visit a site that tells you your IP address. I prefer to search DuckDuckGo for “ip”.
Before setting up ZAP, you should see your home IP displayed:
Afterwards, you should see a completely different IP.
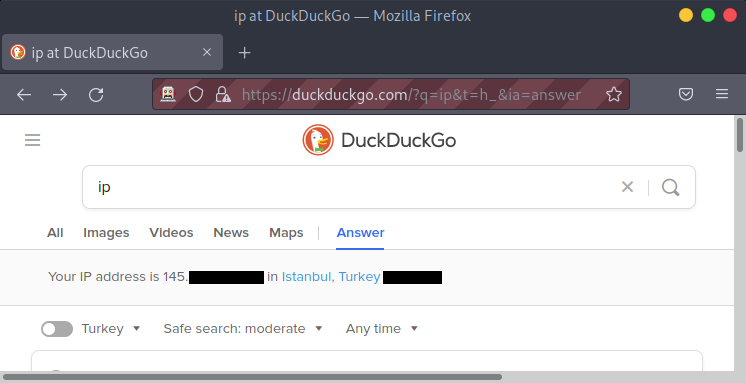
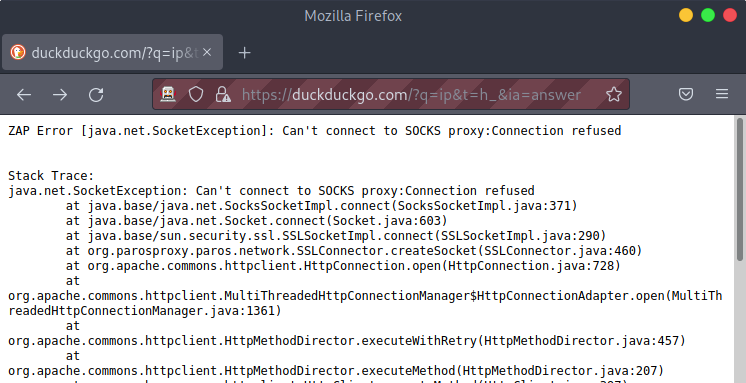
Also, after setting up ZAP, if you break the connection to the VPS, then you will get a “Can’t connect to SOCKS proxy: connection refused” error.
So as long as you set the ZAP proxy settings correctly and you only use a browser that sends its traffic through ZAP, then your home IP will be hidden. This avoids nasty surprises that can happen with virtual private networks (VPNs) where traffic is sent directly from your home IP if the VPN is disconnected for some reason.